Secrets are an important part of any CI/CD pipeline as they allow you to store sensitive data such as API keys, passwords, certificates, and SSH keys. In Semaphore, we already offer the ability to store secrets on an organizational level, and today we are offering an extra level of security by introducing project-based secrets. Project-based secrets are limited to the project where they are set up and can not be used outside the project scope.
Best practices for secrets
The principle of least privilege should be followed when establishing access control on an organizational and project level. This means that a user that is present in your project should only have access to the specific data, resources and applications needed to complete a required task. So we want to separate our secrets by the following criteria:
- Teams that are using them
- People that need them
- Projects that need them
- Reusability
Organization example
Let’s say our organization is called Friendly Traffic Light and we have two projects in our organization, Green Light 🟢 and Blue Light 🔵. Our team consists of the following fictional members that work on both projects:
- Cordelia 🧑💼 who works on 🟢 🔵
- Sydney 🧔 who works on 🟢
- Zainab 🥷 who works on 🔵
The data that we use in our pipelines is:
- An analytics key that is common for all projects (let us mark this as ⚙️)
- AWS deployment data (each project has their own AWS account, project green light has 🗝️ and project blue light has 🔑)
By the principle of least privilege, the project green light and project blue light team should only see their own AWS environments, that is why we put that data in the project secrets accordingly, while the analytics environment is common knowledge, that is why we put it in the organization secrets.
In the end we have the following secrets structure (as can be seen by the people in our organization):
| Person | Secrets available to person | |
| Cordelia | 🧑💼 | ⚙️🗝️🔑 (analytics, AWS for green light and AWS for blue light) |
| Sydney | 🧔 | ⚙️🗝️ (analytics, AWS for green light) |
| Zainab | 🥷 | ⚙️🔑 (analytics, AWS for blue light) |
Setting up in Semaphore
Project secrets are edited the same way as organization secrets. To setup a project secret in Semaphore, just do the following:
Go to your Project and click on Settings:
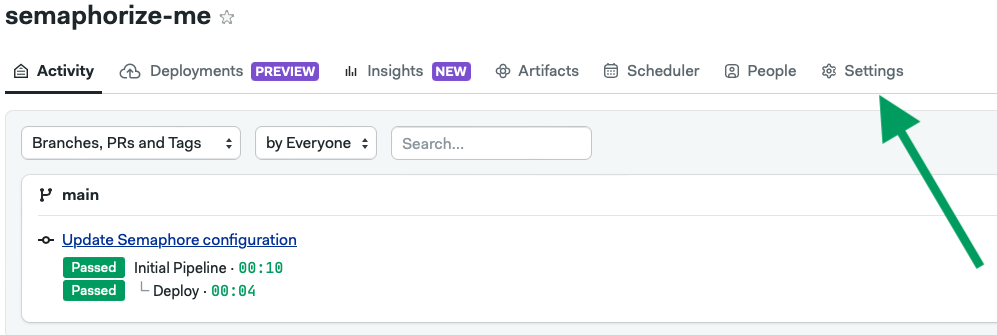
Click on the Secrets tab and then on the Add new button.
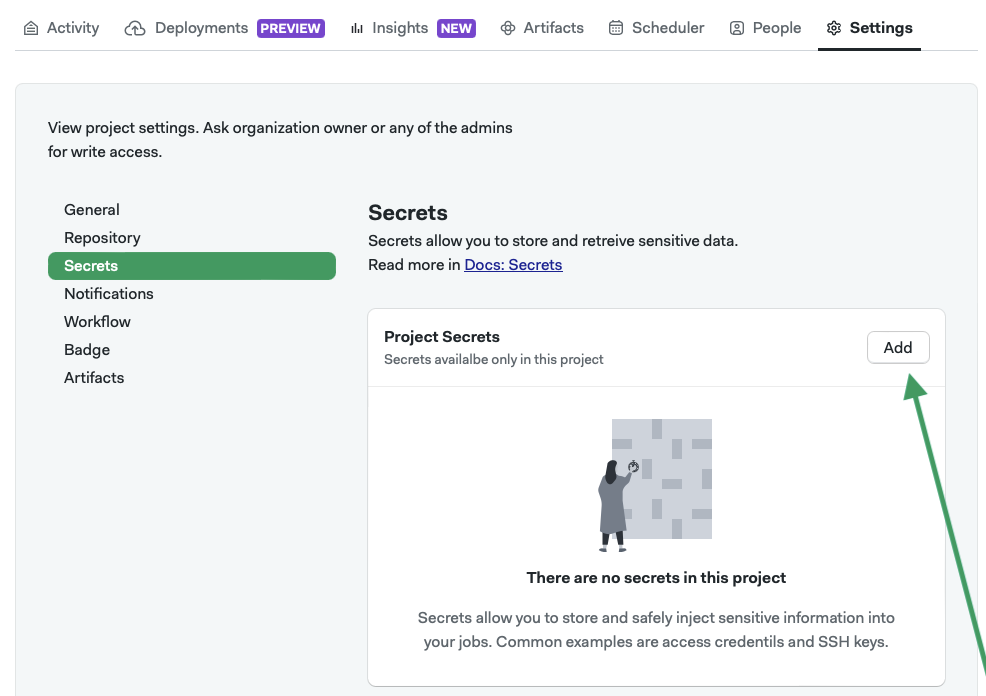
Now you can name your secret and add environment variables or configuration files just like you would be using organization secrets.
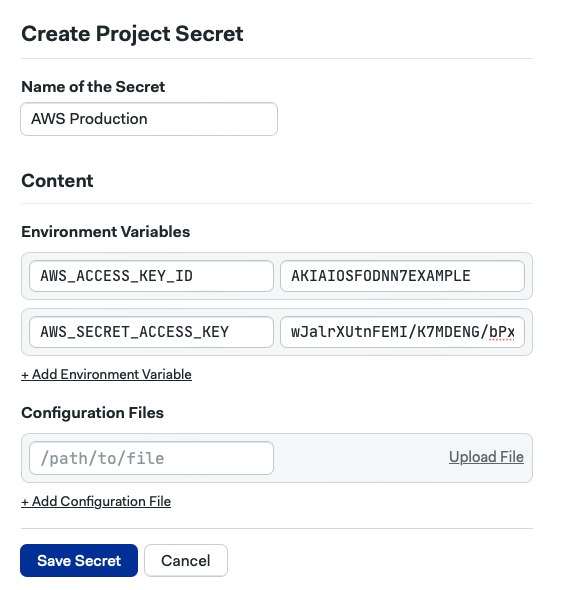
Click on Save Secret.
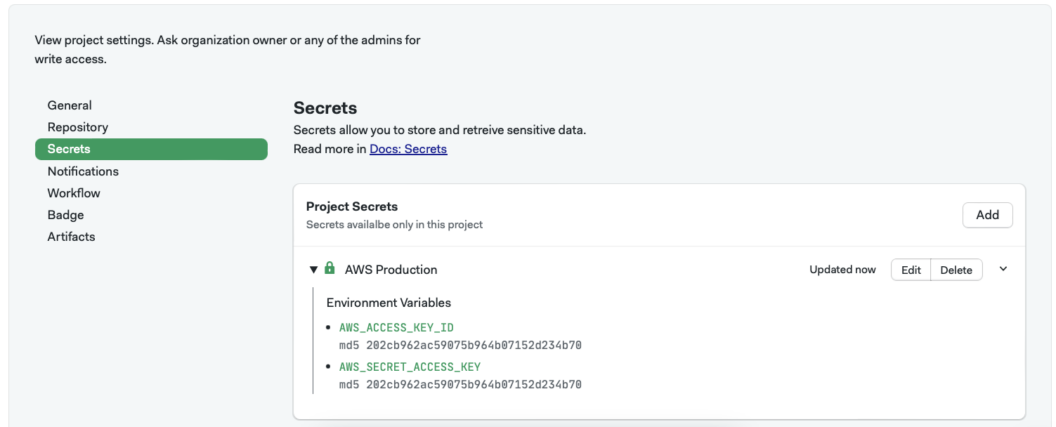
Upon Save you should have the following view with added environment variables:
To use the secrets in your blocks, edit a block and expand the secrets section:
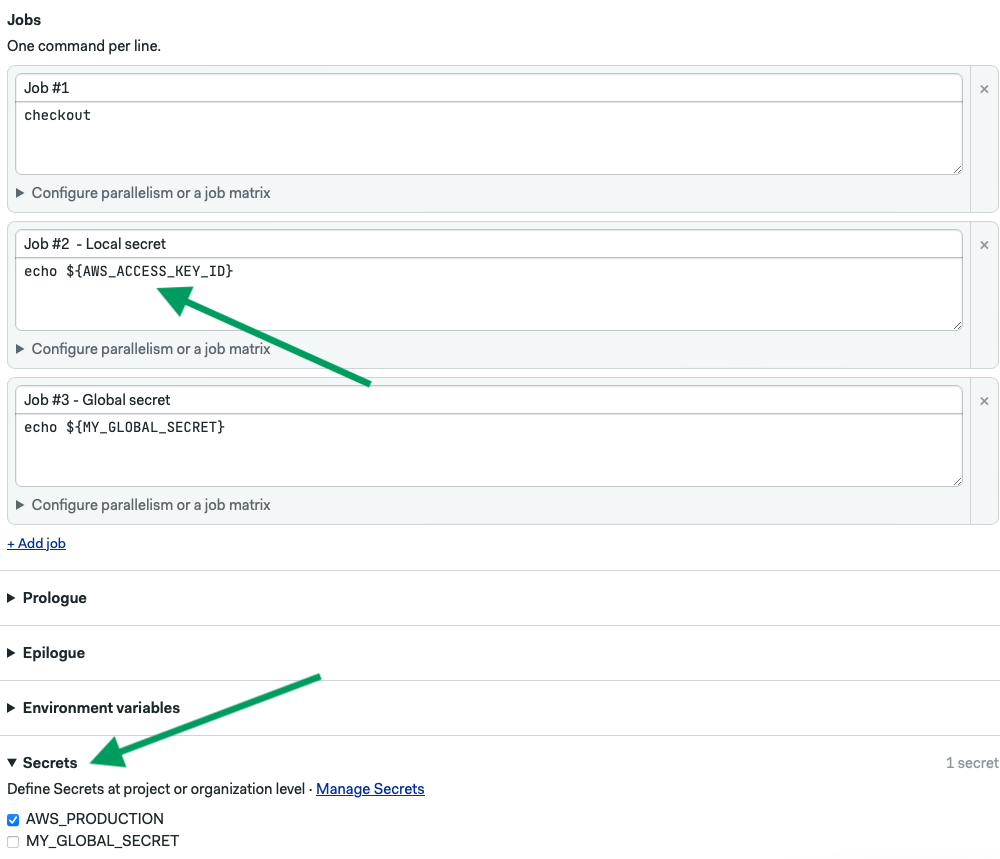
Project Secrets Demo
You can also check the following video on how to setup the organization example we have shown above.
Would you like to know more about secrets?
Make sure to check out the docs to learn more about the feature.
Happy building!
Want to discuss this article? Join our Discord.
